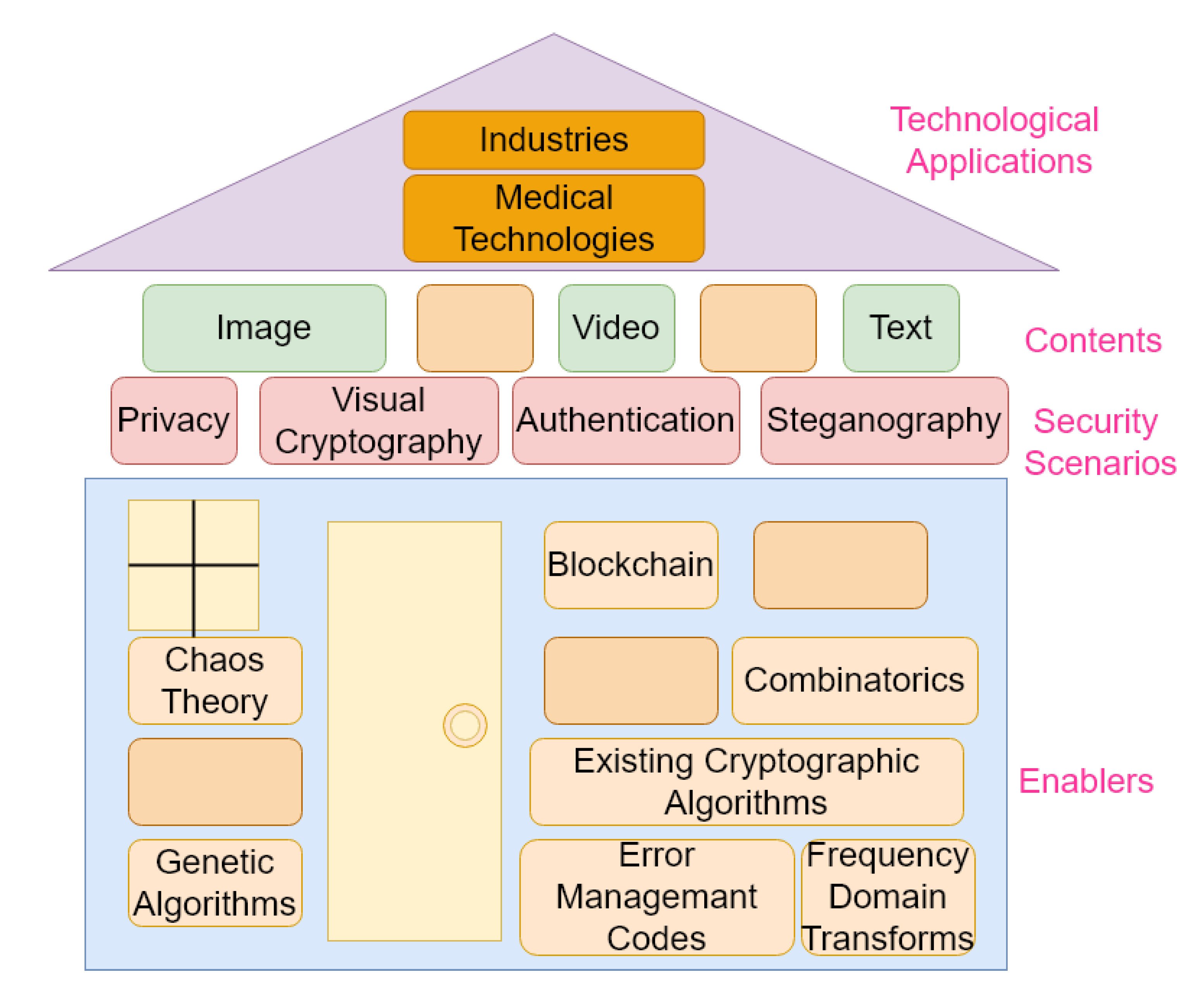
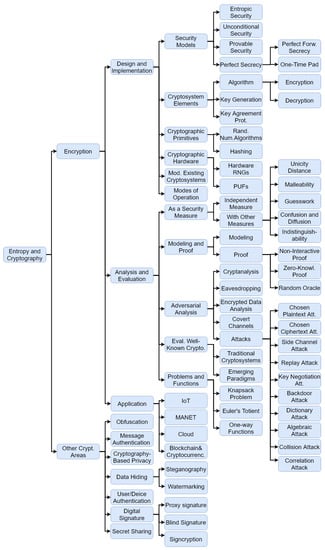
PCHET: An efficient programmable cellular automata based hybrid encryption technique for multi-chat client-server applications - ScienceDirect
Mathematics | Free Full-Text | Cryptographic Algorithm Based on Hybrid One-Dimensional Cellular Automata
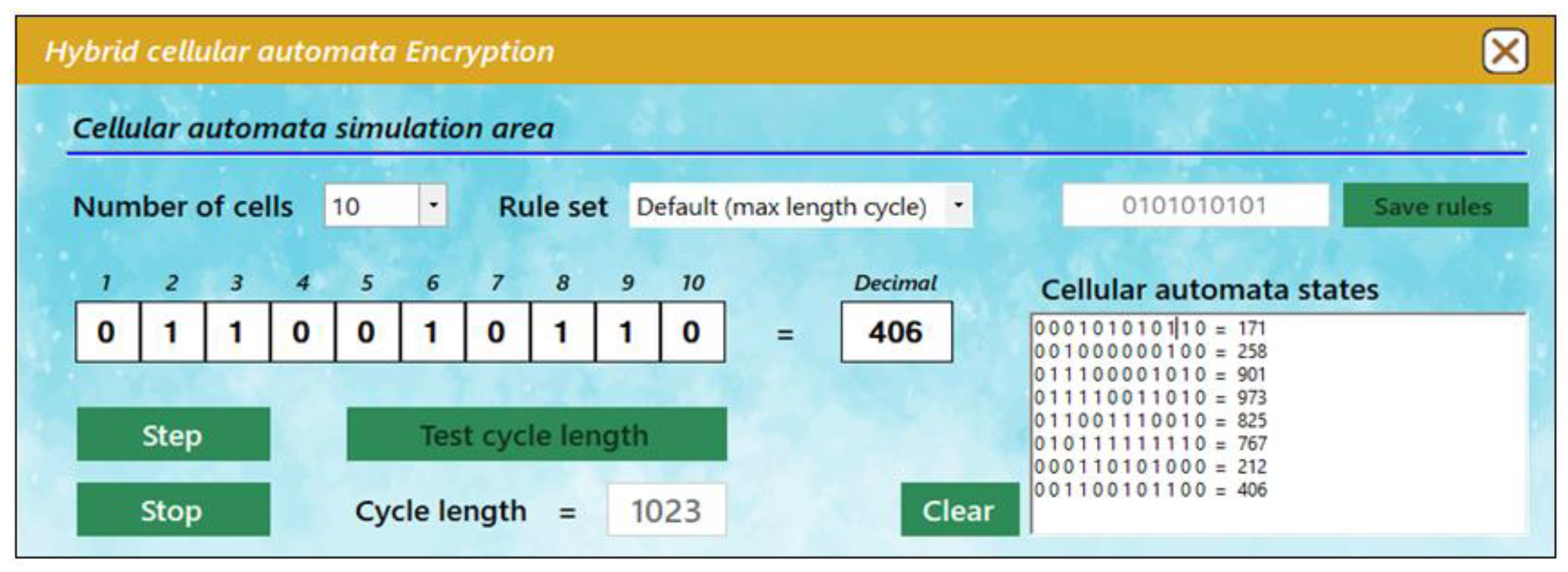
Mathematics | Free Full-Text | Cryptographic Algorithm Based on Hybrid One-Dimensional Cellular Automata

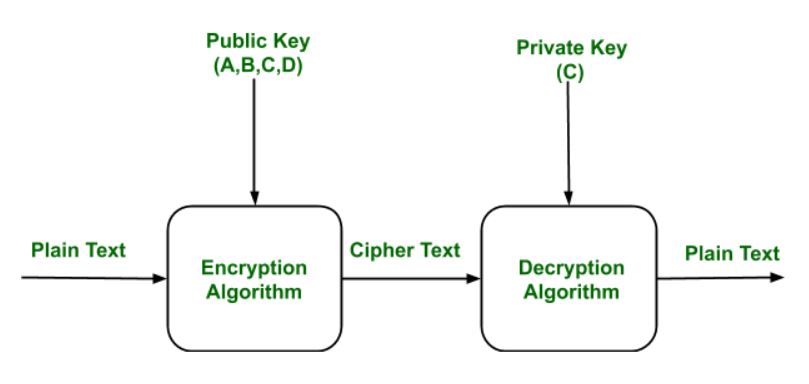
PDF) Security of Telemedical Applications over the Internet using Programmable Cellular Automata | Petre Anghelescu - Academia.edu
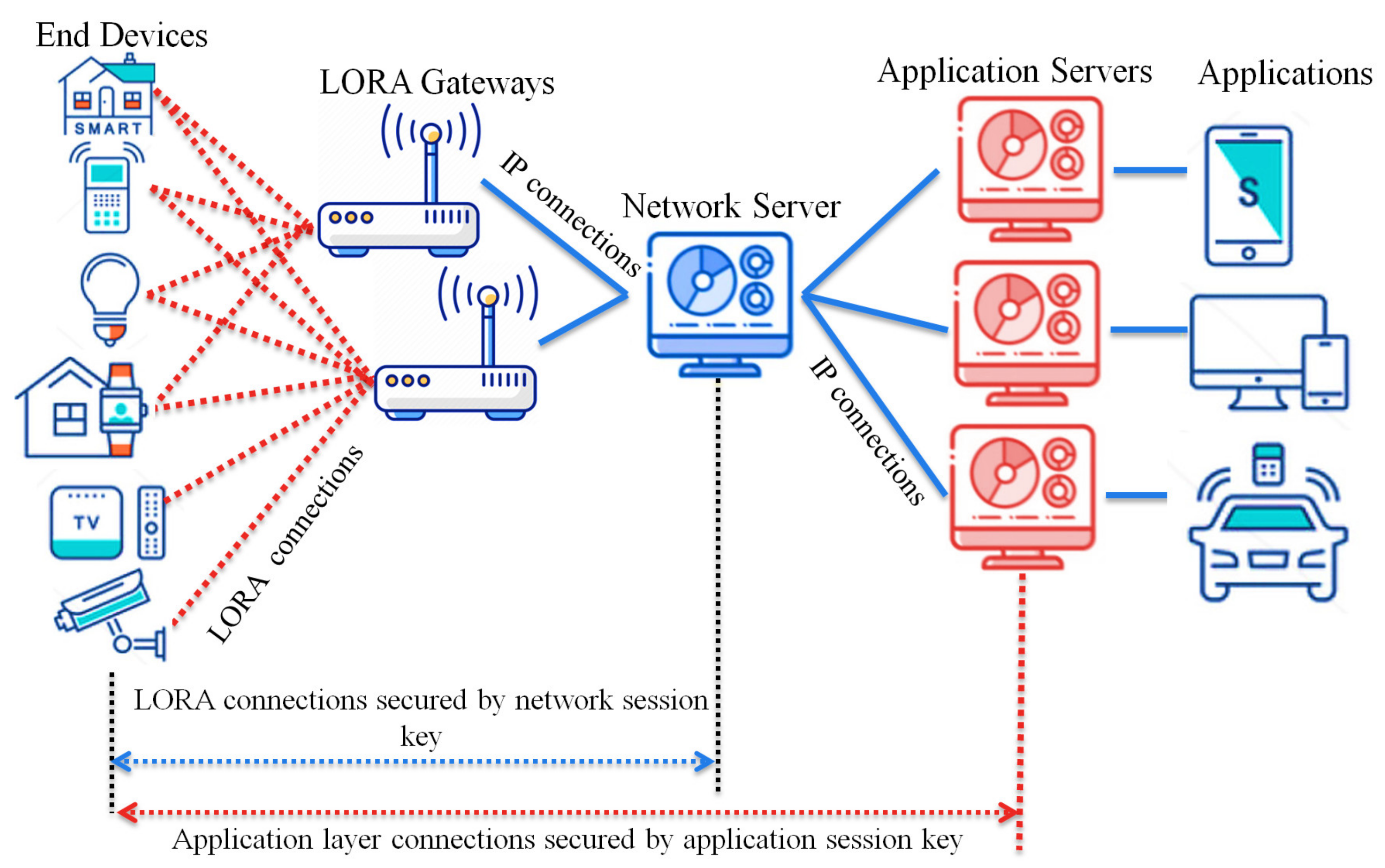
Sensors | Free Full-Text | A Key Management Protocol Based on the Hash Chain Key Generation for Securing LoRaWAN Networks
![PDF] A Lightweight Cellular Automata Based Encryption Technique for IoT Applications | Semantic Scholar PDF] A Lightweight Cellular Automata Based Encryption Technique for IoT Applications | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/19fc3d51392b69ea11e436a91eda596b6c613c53/4-Figure2-1.png)
PDF] A Lightweight Cellular Automata Based Encryption Technique for IoT Applications | Semantic Scholar
![PDF] A New Cryptographic Hash Function Based on Cellular Automata Rules 30 , 134 and Omega-Flip Network | Semantic Scholar PDF] A New Cryptographic Hash Function Based on Cellular Automata Rules 30 , 134 and Omega-Flip Network | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/1563c58daf7a9f63784ee19a98aeb529b7eb66bb/5-Table2-1.png)
PDF] A New Cryptographic Hash Function Based on Cellular Automata Rules 30 , 134 and Omega-Flip Network | Semantic Scholar

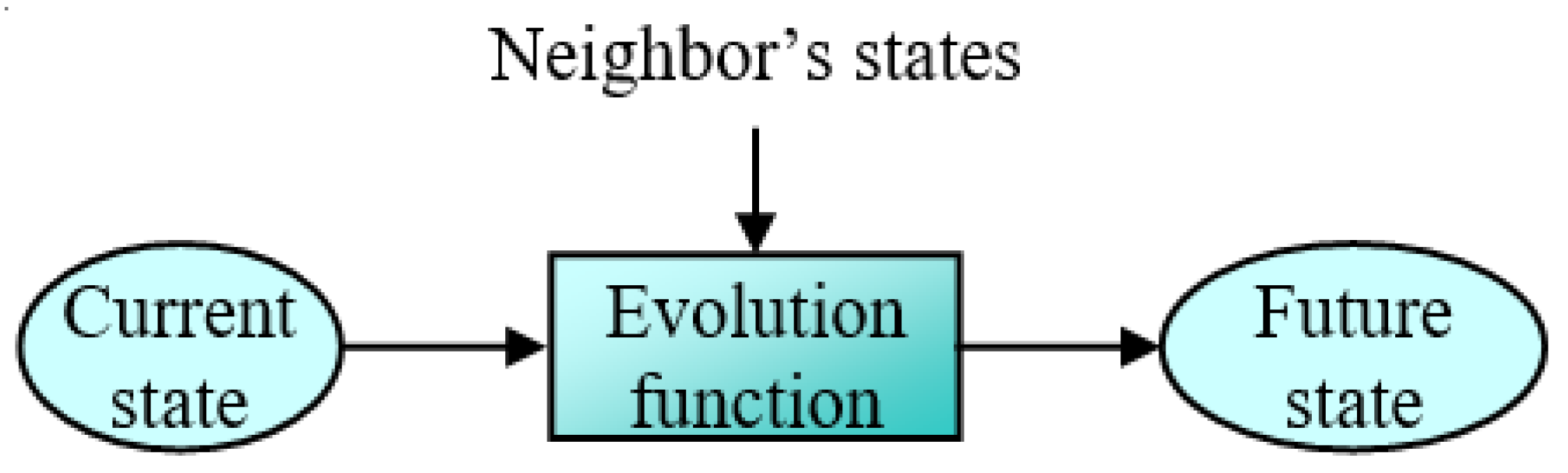
![PDF] On the Applications of Cellular Automata and Artificial Life | Semantic Scholar PDF] On the Applications of Cellular Automata and Artificial Life | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/59885b8e0600b82a8274788ba067b6494dfe3f1b/1-Figure1-1.png)